Cybersecurity should be integrated into the overall safety life cycle for a plant.
Cyber attacks are a growing risk to critical infrastructure and security vulnerabilities have been exposed in industrial control systems (e.g. Stuxnet, Industroyer, TRISIS/TRITON, NotPetya, EKANS, and co.). Many national governments have implemented legislation that requires Operators to systematically assess new or existing plant from a cyber-security perspective. In Germany, for instance, the IT Security Act (IT-Sicherheitsgesetz) and Regulations for Critical Infrastructure Protection (Verordnung zur Bestimmung Kritischer Infrastrukturen, BSI-KritisV) apply. Recommended practices such as those of the Commission on Process Safety (e.g. KAS-44, KAS-51) or the Committee for Industrial Safety (ABS Empf BS 1115) give further guidance.
When to carry out a cybersecurity analysis?
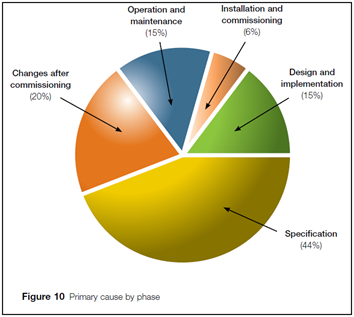
Cybersecurity should be integrated into the overall safety life cycle for a plant. Internationally, best practice standard IEC EN 61511-1 defines that the initial security risk assessment shall be already carried out in the project analysis phase. Further detailed security assessment (including audit of existing plant where applicable) should be carried out as per IEC 62443-3-2 (issued in 2020). The driver to carry out risk analysis (including cyber risk) at an early stage is evident from the well-known UK-HSE study (Out of control: Why control systems go wrong and how to prevent failure), which identified that 65% of the failures in safety systems originated during the design, specification and implementation phases, i.e. prior to operation.
There is every reason to expect that failures in cyber-security measures will also largely have their origin during the design and implementation phases. Therefore it makes sense to follow a cybersecurity life cycle approach as outlined in IEC 62443, in a similar way to the functional safety life cycle as defined in IEC 61511.
Integration of cybersecurity into the risk analysis
The question is how to integrate the cyber-security lifecycle into the established risk management process. Designers and Operators are familiar with ‘traditional’ technical risk management process: concept or FEED-stage PFDs, P&IDs and C&E chart are subject to risk review analysis such as HAZOP and LOPA. SLC management activities as per IEC EN 61511 are applied to the identified safety instrumented functions (SIFs). Historically, cybersecurity issues have only been superficially addressed in the HAZOP (if at all) under ‘Other’ deviations, and tend to be one-liners, such as:
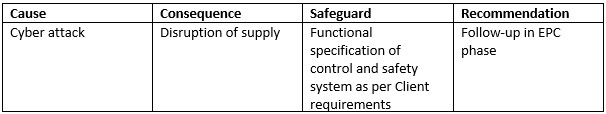
The above is obviously insufficient considering the increasing threat of cyber attack and need to integrate cybersecurity into project design at an early stage. A robust cyber-analysis according to IEC 62443 requires appropriate documentation and qualified team members. Cyber-HAZOP documentation includes, for instance: System Architecture Diagram, Zone & Conduit Drawings, Cyber Network Schematics. Additional experts should participate in the Cyber-HAZOP, including: IT-Manager, (Cyber)security Manager and SCADA/Telecom Engineer. Techniques such as Control Hazard and Operability Study (CHAZOP) paired with a cybersecurity High-Level Risk Assessment (HLRA) in line with IEC 62443-3-2 may be used. HAZOP software such as the CyberPHAx module from ExSILentia allows following similar risk identification / mitigation methodology as per a ‘standard’ HAZOP, with nodes and guidewords adapted to cyber-risks. Completion of a ‘Cyber Security Checklist’ prior to the CHAZOP can identify significant gaps.
At the time of the first project HAZOP, Cyber Security design documentation may not be available, so that a risk analysis as described above is not possible. Nevertheless, PSC recommends to include the deviation ‘Cybersecurity’ alongside the ‘traditional’ HAZOP deviations (see below).
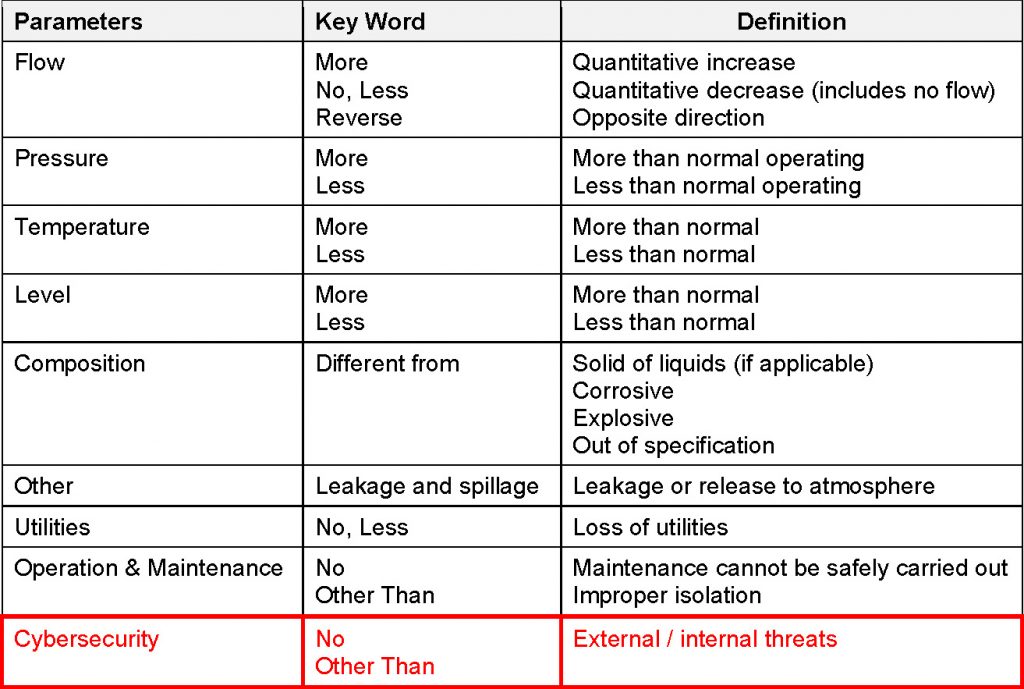
This approach allows a ‘high-level’ first pass cyber-review during the initial HAZOP and ensures, by use of appropriate HAZOP-recommendations, that further cyber-security actions are anchored into the overall project risk management, action tracking, management of change, etc. In particular, cyber requirements impacting procurement (e.g. remote maintenance capability, BPSC/ESD configuration, IT/OT interfaces), should be actioned at an early stage in order to avoid non-conformances and/or cybersecurity gaps that may require costly correction measures during the subsequent Implementation Phase.
PSC has provided independent Chairman and Scribe services for >100 HAZID, HAZOP (including HAZOP revalidation) and LOPA studies. PSC experts are certified according to IChemE and the Exida CFSE program. Please download our HAZOP-SIL-LOPA-References.